The FTC claims on line Health care occupation-teaching business Career Phase focused men and women — such as army servicemembers and spouses — with Untrue advertisements and various unlawful methods. Understand just what the $forty three.five million settlement signifies for a few present and previous college students.
Voice phishing is actually a method of phishing that happens over voice-based media, which include voice about IP -- also known as vishing -- or basic aged telephone assistance. This type of scam works by using speech synthesis software package to go away voicemails notifying the victim of suspicious activity inside of a checking account or credit account.
A way of urgency. They need you to definitely act now. Halt and have a moment to consider the request. Verify the ask for through the use of identified Get in touch with details or details from a general public organization website, not within the message itself.
Spear phishing assaults are directed at specific persons or companies. These assaults usually utilize gathered details precise to the victim to a lot more correctly signify the concept as remaining authentic.
Should you clicked with a url or opened a suspicious attachment, your Personal computer might have malware mounted. To detect and remove the malware, be certain your antivirus software package is up-to-date and it has the most recent patches set up.
Phishing occurs when criminals try to acquire us to open dangerous links, emails or attachments that can request our own info or infect our units.
The phrase phishing was initial Employed in reference read more to your application formulated by a Pennsylvania teen often called AOHell. The program applied a credit score-card-stealing and password-cracking mechanism, which was accustomed to bring about disruptions for AOL.
Protecting against phishing attacks demands a combination of consumer instruction to acknowledge the warning indications and robust cybersecurity systems to halt payloads. Email filters are helpful with phishing, but human avoidance continues to be necessary in cases of Fake negatives.
Only open attachments from the vetted and trusted source. When in doubt, talk to the alleged sender straight. If the sender is non-responsive or imprecise with regard to the context, it would be very best to assume it had been a phishing attempt and report it directly to the IT and/or the safety team.
Get report outlining your stability vulnerabilities that may help you choose speedy action from cybersecurity attacks
/əˈdɔːr.kə.bəl/ (of someone or perhaps a thing) socially uncomfortable or not modern, but in a way which makes you like or like it or them Relating to this Site
With malware installed on qualified user equipment, an attacker can redirect consumers to spoofed websites or produce a payload to your community community to steal data.
Searches Associated with "bokep indonesia terbaru" jilbab bokep indonesia full bokep jepang indonesia thailand bokep indo ter update jilbab ngentot dea onlyfans indonesia colmek indonesia sma japanese mom japanese korea bokep bokep indonesia prank ojol indo bokep indo terbaru indonesia jilbab msbreewc bokep indonesia terbaru 2023 indo crot dalam bokep terbaru bokep indo indonesia terbaru
Comparable to phishing, pharming sends consumers to your fraudulent website that seems to be genuine. On the other hand, In such a case, victims tend not to even really have to click a destructive website link for being taken towards the bogus site.
 Scott Baio Then & Now!
Scott Baio Then & Now! Amanda Bynes Then & Now!
Amanda Bynes Then & Now! Burke Ramsey Then & Now!
Burke Ramsey Then & Now!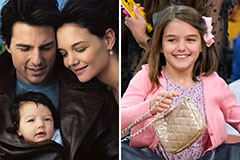 Suri Cruise Then & Now!
Suri Cruise Then & Now!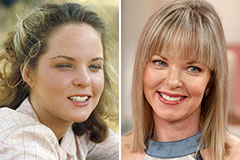 Melissa Sue Anderson Then & Now!
Melissa Sue Anderson Then & Now!